OBSERVING 90 UNTRAINED PARTICIPANTS ABUSING A FLYING ROBOT
The purpose of the project was to present an exploratory study where participants piloted a commercial UAS (Unmanned Aerial System) through an obstacle course. The core hypothesis of this work was that different instructions to the human participant would change how well they performed the task. In particular, we asked participants to fly a robot through an obstacle course. Participants were divided into two groups: one group would be told that the robot was an expensive piece of lab equipment and the other would be told that it was a toy. The study focused on self-reported stress. The purpose of the research was to program robots such that they could look to try and increase or decrease the level of stress by having the experimenters make disapproving vocalizations when the robot crashes or saying calming phrases when the participants make mistakes.
The research project was further carried out in 2016 where we empirically measured stress levels using Galvanic Skin Response and Heart Rate Monitor, while the participants piloted the commercial UAS through the obstacle course. The use of Motion Tracking System also allowed us to record the drone movements through the obstacle course. The purpose of the experiments was to see if the measures correlate with performance. That way, the robot could adjust its performance automatically, such as slowing down the maximum speed when the user is very nervous. The data from Motion Tracking System would be used to program the UAS to pilot autonomously in situations where the user may be incapable to do so during high-stress levels.
| Test | Condition 1 (# participants) | Time (sec) | Condition 2 (# participants) | Time (sec) | Statistically Significant |
| Instructions | Expensive (35) | 31.5 | Toy (42) | 30.7 | No |
| Age | < 30 years (27) | 24.3 | ≥ 30years (48) | 35.1 | Yes |
| Nervousness | Nervous (26) | 35.9 | Calm (43) | 28.4 | Yes |
| Video Games | < 3 hours/week (57) | 33.4 | > 3 hours/week (19) | 24.3 | Yes |
Table: Summary of Statistical Results
Paper Publication: http://irll.eecs.wsu.edu/wp-content/papercite-data/pdf/2015ai_hri-scott.pdf
SECURE WIRELESS TRANSMISSION FOR MOTION MONITORING APPLICATIONS
This project required us to develop a pair of Android applications using Java. The function of these applications was to transfer encrypted files containing the data collected by wireless sensors in an android phone over Bluetooth. The sender android phone was equipped with tri-axial accelerometer and gyroscope (Smart watches was used in our project) for the purpose of recording motion analysis based on the movements of the user. In the project, we used a symmetric key for the purpose of secure transmission among the sender and multiple receivers. In order to reduce the complexity and potential risk in setting and sharing the symmetric key, our application used the Bluetooth MAC address of receiver device as the source to generate the parameters used for data encryption. Therefore, for the same file sharing with multiple receivers, the encrypted file transmitted to each receiver is different from others. Our encryption method contained both substitution and transposition processes. Since a 48-bit MAC address is usually detected as twelve hexadecimal codes, the first two distinct digit characters (1-9) were automatically selected as the numbers for substitution in the entire file. The file is transferred to the receiver android phone using Bluetooth which is enabled in the application by the use of Bluetooth Adapter. Here the File is decrypted using the same algorithm.
HOME SECURITY SYSTEM USING FACE RECOGNITION AND VOICE COMMANDS
The project required me to work on programming the Face Recognition System using MATLAB and implement it alongside Voice Commands to design a functional Home Security System. The Face Recognition Algorithm required two basic operations: Feature Extraction and Classification criterion. The first operation, Feature Extraction, required the use of Discrete Cosine Transform (DCT). Since DCT is data dependent and DCT can be implemented using a fast algorithm, it was advantageous to use it over several other feature extraction methods. The Home Security System would input an image of the user from a webcam and resize the image using Nearest Neighbor Interpolation. The image would be divided into several 8x8pixel blocks where an algorithm would be applied to compress each block using 2D-DCT.
The second operation required the use of Self-Organizing Maps known as Kohonen Map to create an Artificial network of Neurons. Initial input of images is required by the user in order to execute Unsupervised Learning phase to build the Neural Network. The 2D-DCT vectors are used for data during the training phase where for each node, the number of ‘wins’ is recorded along with the label of the input sample. The weight vectors for the nodes are updated. By the end the of training phase, each node of the Self Organizing Maps has two recorded values: the total number of winning times for subject present the in image database and the total number of winning times for subject not present the in image database. During the Testing phase, the preprocessing of user input image takes place and then each input vector is compared with all nodes of the Self Organizing Map and the best match is found based on Minimum Euclidean distance.
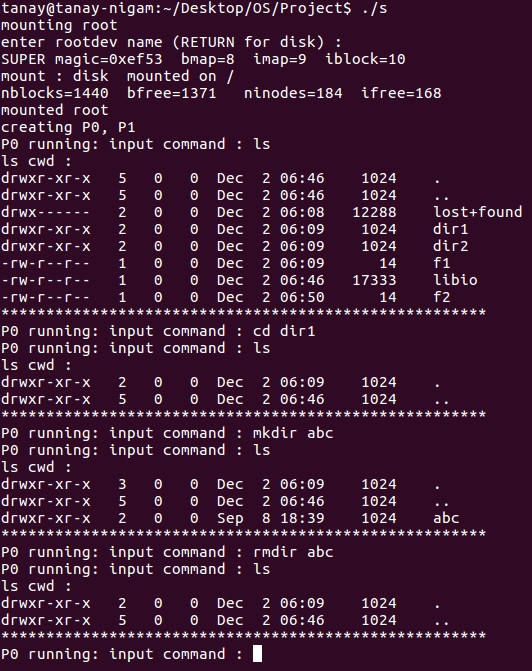
LINUX FILE SYSTEM SIMULATOR
This project required me to implement a File System Simulator. This was done by implementing various File System commands on MTX operating System designed and provided to us by our professor. The commands used various algorithms and system calls to access kernel functions. The process would have to be continuously switched between kernel functions and user mode to obtain the desired result. It required extensive use of C library functions for System calls and a small amount of Assembly programming to execute each instruction. Various instructions implemented include mkdir (make directory), rmdir (remove directory), ls (file listing), pwd (Print Working directory) and many more commands essential for a working File System Simulator. As an example, one such algorithm implemented: File open would require user input file name for ‘READ’ or ‘WRITE’. In user mode, this would then create a File structure in user heap which issues a system call kopen() in kernel. This constructed an ‘Opentable’ to represent an instance of the opened file which contained the file’s open mode, a pointer to the file’s INODE in the memory and current byte offset into the file for read/write. Physical I/O on the I/O buffers ultimately go through the device driver using various interrupt handlers. This allows us to open the File with the user input text name.